
Nothing is completely secure. Locks can be picked, safes can be broken into, and online passwords can be guessed sooner or later. How, then, can we protect the things that we value? One way is to use biometrics—fingerprints, iris scans, retinal scans, face scans, and other personal information that is more difficult to forge. Not so long ago, if you'd had your fingerprints taken, chances are you were being accused of a crime; now, it's innocent people who are turning to fingerprints to protect themselves. And you can find fingerprint scanners on everything from high-security buildings to ATM machines and even laptop computers. Let's take a closer look at how they work!
Why are fingerprints unique?
It's pretty obvious why we have fingerprints—the tiny friction ridges on the ends of our fingers and thumbs make it easier to grip things. By making our fingers rougher, these ridges increase the force of friction between our hands and the objects we hold, making it harder to drop things. You have fingerprints even before you're born. In fact, fingerprints are completely formed by the time you're seven months old in the womb. Unless you have accidents with your hands, your fingerprints remain the same throughout your life.
 What makes fingerprints such a brilliant way of telling people apart is that they are virtually unique: fingerprints develop through an essentially random process according to the code in your DNA (the genetic recipe that tells your body how to develop). Because the environment in the womb also has an effect, even the prints of identical twins are slightly different. While it's possible that two people could be found who had identical fingerprints, the chances of this happening are so small as to be virtually negligible. In a criminal case, there are usually other pieces of forensic evidence that can be used with fingerprints to prove a person's guilt or innocence beyond reasonable doubt. Where fingerprints are being used to control access to something like a computer system, the chances of a random person having just the right fingerprint to gain entry are, generally speaking, too small to worry about—and much less the chance of someone guessing the right password or being able to break through a physical lock.
What makes fingerprints such a brilliant way of telling people apart is that they are virtually unique: fingerprints develop through an essentially random process according to the code in your DNA (the genetic recipe that tells your body how to develop). Because the environment in the womb also has an effect, even the prints of identical twins are slightly different. While it's possible that two people could be found who had identical fingerprints, the chances of this happening are so small as to be virtually negligible. In a criminal case, there are usually other pieces of forensic evidence that can be used with fingerprints to prove a person's guilt or innocence beyond reasonable doubt. Where fingerprints are being used to control access to something like a computer system, the chances of a random person having just the right fingerprint to gain entry are, generally speaking, too small to worry about—and much less the chance of someone guessing the right password or being able to break through a physical lock.
Enrollment and verification
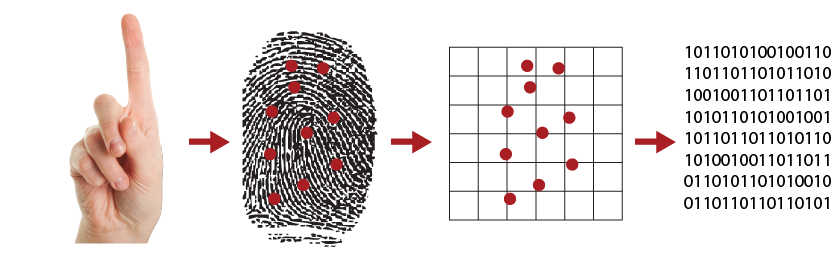
 There are two separate stages involved in using a system like this. First you have to go through a process called enrollment, where the system learns about all the people it will have to recognize each day. During enrollment, each person's fingerprints are scanned, analyzed, and then stored in a coded form on a secure database. Typically it takes less than a half second to store a person's prints and the system works for over 99 percent of typical users (the failure rate is higher for manual workers than for office workers).
There are two separate stages involved in using a system like this. First you have to go through a process called enrollment, where the system learns about all the people it will have to recognize each day. During enrollment, each person's fingerprints are scanned, analyzed, and then stored in a coded form on a secure database. Typically it takes less than a half second to store a person's prints and the system works for over 99 percent of typical users (the failure rate is higher for manual workers than for office workers).
Once enrollment is complete, the system is ready to use—and this is the second stage, known as verification. Anyone who wants to gain access has to put their finger on a scanner. The scanner takes their fingerprint, checks it against all the prints in the database stored during enrollment, and decides whether the person is entitled to gain access or not. Sophisticated fingerprint systems can verify and match up to 40,000 prints per second!
How fingerprints are stored and compared
When fingerprints were first used systematically for criminal investigation in 1900, by Sir Edward Henry of the Metropolitan Police in London, England, they were compared slowly and laboriously by hand. You took a fingerprint from a crime scene and another fingerprint from your suspect and simply compared them under a magnifying glass or microscope. Unfortunately, fingerprints taken under different conditions can often look quite different—the one from the crime scene is much more likely to be incomplete or smudged—and comparing them to prove that they are identical (or different) sometimes takes great skill. That's why forensic scientists (people who study evidence collected from crime scenes) developed a reliable system for matching fingerprints where they looked for between eight and sixteen distinct features. In the UK, two fingerprints need to match in all sixteen respects for the prints to be judged the same; in the United States, only eight features need to match.
When a computer checks your fingerprints, there obviously isn't a little person with a magnifying glass sitting inside, comparing your fingerprints with all the hundreds or thousands stored in the database! So how can a computer compare prints? During enrollment or verification, each print is analyzed for very specific features called minutiae, where the lines in your fingerprint terminate or split in two. The computer measures the distances and angles between these features—a bit like drawing lines between them—and then uses an algorithm (mathematical process) to turn this information into a unique numeric code. Comparing fingerprints is then simply a matter of comparing their unique codes. If the codes match, the prints match, and the person gains access.
How fingerprint scanners work
Having your fingerprints taken at a police station involves pressing your fingers onto an ink pad and then rolling your fingers onto paper to leave a clean impression on the page. Your prints are also stored on a computer database so the police can check if you've committed any known crimes or if you do so in future.
But when fingerprints are being used to control access to buildings and computer systems, more sophisticated methods have to be used: a computer has to scan the surface of your finger very quickly and then turn the scanned representation into a code it can check against its database.
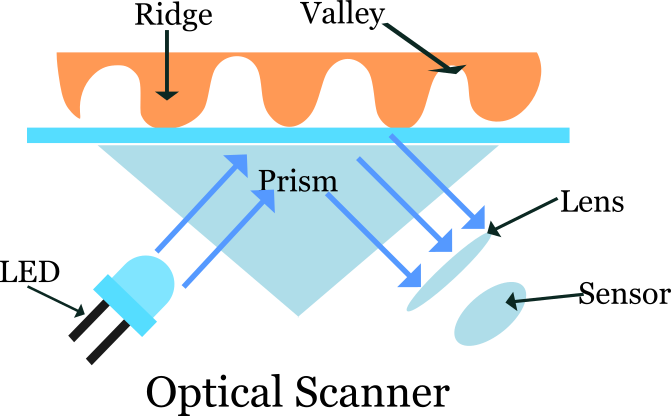
There are two main ways of scanning fingers. An optical scanner works by shining a bright light over your fingerprint and taking what is effectively a digital photograph. If you've ever photocopied your hand, you'll know exactly how this works. Instead of producing a dirty black photocopy, the image feeds into a computer scanner. The scanner uses a light-sensitive microchip (either a CCD, charge-coupled device, or a CMOS image sensor) to produce a digital image. The computer analyzes the image automatically, selecting just the fingerprint, and then uses sophisticated pattern-matching software to turn it into a code.
Another type of scanner, known as a capacitive scanner, measures your finger electrically. When your finger rests on a surface, the ridges in your fingerprints touch the surface while the hollows between the ridges stand slightly clear of it. In other words, there are varying distances between each part of your finger and the surface below. A capacitive scanner builds up a picture of your fingerprint by measuring these distances. Scanners like this are a bit like the touchscreens on things like iPhones and iPads.






0 Comments
Please do not add any spam link in comment box